Google's Project Zero vulnerability research team identified serious flaws in Zoom that were patched on May 17, allowing hackers to launch zero-click attacks on devices running the messaging app, Ars Technica reported.
The vulnerabilities, known as CVE-2022-22786 and CVE-2022-22784, allowed cybercriminals to carry out attacks even if the victim did nothing but keep the client open. Inconsistencies in how the Zoom client and Zoom servers interpret XMPP messages allowed "smuggling" of content that would normally be prohibited, according to Google Project Zero researcher Ivan Fratric.

Critical Vulnerability in Zoom
This report, as per Fratric, presents a vulnerability chain that allows a malicious attacker to compromise another user over Zoom chat. Successful exploitation does not necessitate user interaction because the sole requirement for the attacker is the ability to send messages to the victim via Zoom chat using the XMPP protocol.
How Does This Flaw Work?
According to Fratric, the first vulnerability (dubbed XMPP Stanza Smuggling) takes advantage of parsing mismatches between Zoom's client and server XML parsers to "smuggle" arbitrary XMPP stanzas to the victim client.
The attacker can then force the victim client to connect to a hostile server by providing a specially designed control stanza, effectively turning this primitive into a man-in-the-middle attack.
Read More : Some Honda, Acura Models Affected by Vulnerability That Lets Hackers Unlock and Start the Car
Finally, the victim client downloads and runs a malicious update after intercepting/modifying client update requests/responses, resulting in arbitrary code execution.
A client downgrade attack is used to get beyond the update installer's signature check. This attack was demonstrated using the current (5.9.3) client on Windows 64-bit. However, portions of the chain are likely relevant to other systems.
How Critical Is It To Have Automatic Updates?
Zoom added automatic updates to its macOS and Windows clients in December. The severity of the vulnerabilities shows the significance of the auto update addressed last week. Hackers frequently reverse engineer updates like this within hours or days of them becoming accessible and use them as an exploit road map, per the report of Ars Technica.
Techniques for Preemptively Hijacking Internet Accounts
Zoom is not the only app that was subjected to vulnerability.
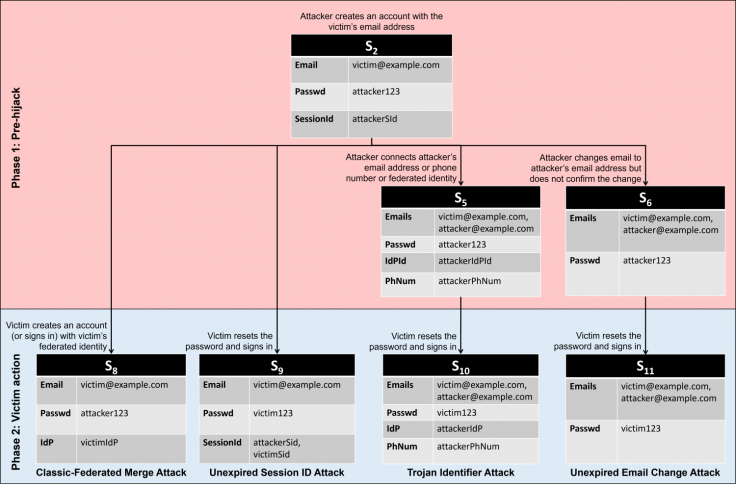
As previously reported, a paper titled "Pre-hijacked accounts: An Empirical Study of Security Failures in User Account Creation on the Web," found that there are five related techniques for preemptively hijacking internet accounts.
1. Classic-Federated Merge Attack: This takes advantage of a vulnerability in the interaction between the conventional and federated account creation processes.
2. Unexpired Session Identifier Attack: This exploits a vulnerability in which authenticated users are not automatically signed out of an account when they reset their password.
3. Trojan Identifier Attack: This takes advantage of the attacker's ability to connect an additional identifier to an account created using the typical username and password procedure.
4. Unexpired Email Change Attack: This makes use of a potential vulnerability in which the service fails to invalidate email-change capability URLs after a user changes their password.
5. Non-Verifying IdP Attack: This is the mirror image of the Classic-Federated Merge Attack. When creating a federated identity, the attacker uses an IdP that does not validate ownership of an email address.