Microsoft investigated an attack from threat actors, who targeted cryptocurrency investment companies on Telegram. The hacker group reportedly joined chat groups to facilitate the conversations, between VIP clients and crypto exchange platforms. Through this method, the threat actors identify potential victims.
'DEV-0139' Hacker Group
The threat actors have been tracked by Microsoft as DEV-0139. After identifying their target from Telegram chat groups, they will claim to be representatives of other crypto asset management firms as well. They will then invite clients to join another Telegram group, wherein they will ask for feedback regarding the fee structure of crypto exchange platforms.
They also appear to know about the workings of the cryptocurrency industry, as well as the challenges that come with it. This shows that the hackers are actually well-prepared for the cyberattacks, making them appear more legitimate to their potential victims. They will ask questions about fee structures as well as crypto platforms used for trading.
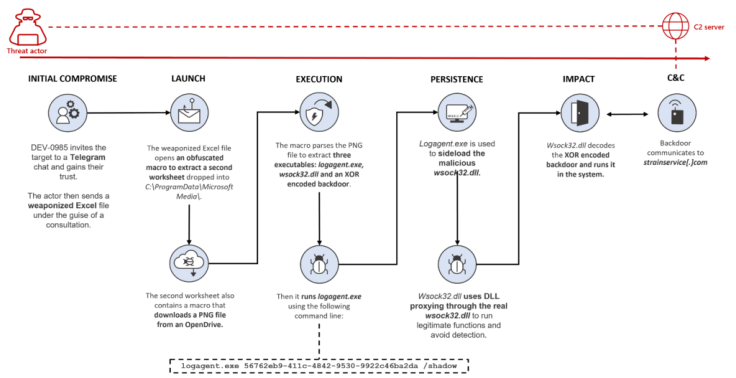
The hackers would slowly gain the clients' trust before sending an infected Excel spreadsheet, containing data comparisons of VIP fee structures in various crypto exchange companies. The file is named "OKX Binance & Huobi VIP fee comparision.xls," which is protected by a password dragon so targets would enable macros.
Once the macros have been enabled, another worksheet included in the file would download a PNG file. That file extracts a malicious DLL, an XOR-encoded backdoor, and a Windows executable that will be used to sideload the extracted DLL. Once the DLL loads the backdoor, the threat actors will have remote access to the target's system, as mentioned by Bleeping Computer.
Similar Attack
Microsoft has also discovered a different file, containing the same logagent.exe mechanism, which also delivers the same payload. The loader will appear as an MSI package, which poses as an application called CryptoDashboardV2. Once installed, an application called tplink.exe would sideload a DLL or a DLL proxy.
When the payload has been decoded in the memory by the DLL, the threat actor may access the device where the malicious file was downloaded. It will retrieve information from the targeted system and then connect back to a remote server which will send out commands, according to Microsoft.
How to Avoid the Attacks
You could change your macro security settings since the attack begins once the target has enabled it. You'll be able to control which macros will run in different circumstances once you open a file. Targets will be able to stop malicious XLM or VBA macros, by scanning files with Antimalware Scan Interface (AMSI).
Usually, this is enabled by default. You can check if the Group Policy setting for Macro Run Time Scan Scope is actually set to "Enable for All Files" or "Enable for Low Trust Files," just to be on the safe side. Make sure that your system's antivirus is also up to date, and that real-time monitoring is on.
For this kind of attack specifically, you may turn on attack surface reduction rules. This will target suspicious software behaviors, such as launching executable files and scripts, attempting to download or run files, running obfuscated or suspicious scripts, or performing behaviors that apps don't usually do on a daily basis.









