A researcher who found a bug in the Google Home smart speaker last year published a blog about the issue. He explained in detail how a backdoor account could be used to control the device remotely, which can then be turned into a device that allows hackers to listen to conversations.
Google Home Flaw
The researcher experimented on his Google Home mini speaker, wherein he found out that adding new accounts through the Google Home app allows him to send remote commands. He did so through the cloud API of the system.
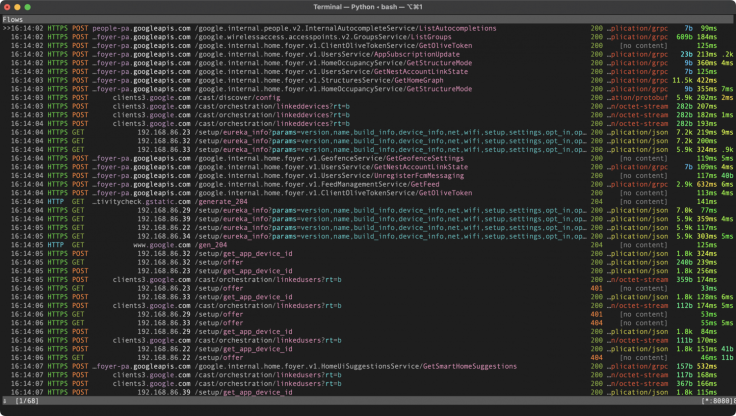
He posted a screenshot of the encrypted traffic, which was captured using a setup proxy in the port for the local HTTP API of Google Home. The process needed to add a user requires the device name, certificate, and cloud ID from the local API, as mentioned in Bleeping Computer.
According to the researcher, intercepting HTTPS traffic was tricky but not difficult. After tinkering with the proxy settings, all you need to do is get the app to trust the proxy's root CA certificate. He added that new CA certificates can easily be downloaded through Android settings.
However, there are restrictions. Android 7 apps use networking APIs that come with the system will automatically block CA certificates added by third parties. Users can still patch individual apps manually, given that it does not pin SLL.
The researcher mentioned that if the app does use APIs provided by the system or a known HTTP library, you can bypass it by using relevant methods with Frida or Xposed, although you'll have to reverse engineer the pinning mechanism and patch it out if the app has a custom mechanism.
That's where you might hit a snag since according to his blog, the Google Home app uses Google Play Services OAuth APIs. That means that APKs that aren't signed by Google will crash when you patch and repack them.
This led the researcher to intercept traffic with root access using his old phone and Magisk. He modified the system CA store and included the proxy's CA. He also used a Frida script on GitHub to bypass the pinning mechanism.
Once he got past all the barriers, he managed to see the encrypted traffic show up in mitmproxy himself. He added that the traffic between the app and the device was also captured, which he showed in a series of screenshots.
The Security Risk
The blogger provided possible attack scenarios should the flaw be exploited. When a hacker wants to spy on a victim, they can have the victim install a malicious Android app, which will detect Google Home on the network through mDNS.
The app will then use LAN access to send out two HTTP requests to link the attacker's account to the device. This can all be done without permission which allows the attacker to now spy on the user through Google Home.
Another scenario is a hacker discovering the victim's Google Home by listening for MAC addresses, given that they have prefixes associated with Google Inc. The hacker can then make the device enter setup mode by disconnecting it from the network with deauth packets.
Once the hacker has connected to the device's setup network, they can access the device information. They can then connect to the internet and use that information to link their own account to the victim's device.
Of course, it will no longer work for Google Home devices that have the latest firmware version. The researcher also reported the potential exploit to Google last year, wherein Google rewarded him with $107,500 for doing the responsible thing.









