
CI/CD pipelines have become an integral part of modern software development and deployment. They enable the process of building, testing, and delivering code changes to be automated, allowing developers to efficiently introduce new features and bug fixes to users.
However, as with any automated process, potential security risks should not be overlooked. Any vulnerability or flaw within a pipeline could compromise the security of the entire system. Therefore, it is crucial to prioritize security throughout the pipeline's life cycle to ensure the protection of sensitive data and mitigate the risk of cyber attacks.
Security threats can emerge in various parts of a CI/CD pipeline, from the configurations and code of the pipeline to incorrect integration with other systems, such as source code repositories and cloud infrastructure. To minimize the attack surface of the pipeline, security measures must be integrated at every step of development and deployment.
By identifying and mitigating potential security vulnerabilities at every step, developers can ensure the integrity of the system and protect sensitive data from cyber threats. Prioritizing security in the planning and execution of any CI/CD process is crucial to ensure the success and security of modern software development and deployment.
Methods to Build Secure and Agile CI/CD Pipelines
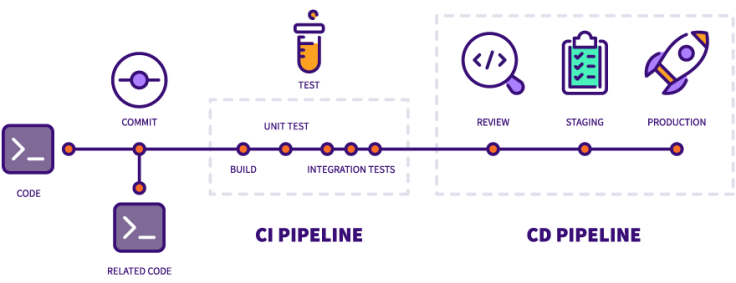
Building secure and agile CI/CD pipelines can be accomplished in various ways. However, these ways involve careful planning and execution of techniques to handle potential security issues and guarantee quick and reliable deployment of code changes. CI/CD security can only be achieved by thorough planning to guarantee that every component is securely fastened. Let's talk about several crucial technical tactics that can aid developers in creating CI/CD pipelines that are both secure and flexible. They comprise security evaluations and appropriate privileges.
Secure Infrastructure as Code (IaC)
Infrastructure as code (IaC) is the practice of treating infrastructure as if it were code. It involves defining and provisioning infrastructure through code rather than manual setup, allowing for the automation of infrastructure deployment and configuration. This results in a quicker and more reliable process.
To ensure the safety and adherence to industry standards, best practices such as avoiding hard-coded secrets like API keys and access tokens must be followed. Instead, secret managers should be utilized, even in secure network setups with correct policies and scanning. Secret managers provide a more secure way of storing sensitive information, making them a recommended choice for IaC code.
Using Microservices or Containerization for Deployment
Security is a primary consideration in containerization and CI/CD. While containerization provides portability, scalability, and ease of deployment, it also introduces new vulnerabilities in data security. Even though containers are designed to operate independently from the host system, security flaws can arise if the container image has vulnerabilities or if the configuration settings are incorrect.
Thus, precautions such as image scanning, the application of least possible privileges, and restricted access to host containers are recommended. Least privileges should be applied to ensure that only authorized users have access to different microservices. Given that potentially dangerous images could jeopardize the entire ecosystem, accurate and timely scanning and evaluation processes are necessary.
Implement Continuous Security Testing
Continuous security testing involves integrating security testing into every stage of the CI/CD pipeline to ensure that vulnerabilities are discovered and resolved before code changes are distributed. Teams must consider threat models such as STRIDE, and deployment pipelines should be equipped with SSDLC.
The process starts with threat modeling, followed by the use of automated security testing tools like static code analysis during code deployment and dynamic application security testing (DAST) when the code is live in production to scan for vulnerabilities in real-time and address any issues that may arise. In the final stage, penetration testing should be conducted to identify problems that may have been missed during the initial lifecycle.
Use Immutable Infrastructure
Immutable infrastructure emphasizes the use of artifacts that are created once and never changed, such as machine images or container images. Previous infrastructure models allowed for modifications to be made to running servers, resulting in configuration drift and potential security vulnerabilities caused by out-of-date software or configuration issues.
With immutable infrastructure, modifications are made by generating new artifacts, which are tested and deployed to replace previous ones. This approach eliminates configuration drift and provides a stable, reproducible, and secure infrastructure. Moreover, maintaining version control contributes to a secure infrastructure, further enhancing the overall security of the system.
Implement Proper Logging and Monitoring
To identify and respond to security incidents, comprehensive logging and monitoring should be implemented throughout the CI/CD pipeline. This includes checking logs for any suspicious activity, utilizing intrusion detection systems with incident response capabilities, and implementing security information and event management (SIEM) solutions. Logging and monitoring systems enable early detection and rapid resolution of potential security breaches.
Furthermore, these systems help determine the resources that were lost or stolen and the actions that were taken, which is crucial for incident response. Therefore, it is highly recommended to implement logging and monitoring throughout the entire pipeline to enhance the overall security of the system.
Conclusion
Developing secure and agile CI/CD pipelines requires a comprehensive approach that incorporates various technical tactics, including containerization, implementing security as code, using automated testing, and continuous feedback. Microservices can also be utilized to enhance the security of the pipeline.
By implementing these strategies, organizations can ensure that their code is secure, their infrastructure is correctly configured, and security incidents are detected and addressed quickly. This helps reduce the risk of financial losses, reputational harm, and data breaches resulting from security incidents. Building secure and agile continuous integration and continuous delivery pipelines is essential for the success of modern software development projects at scale.









