
As more and more Americans transition to a near-entirely digital existence, new threats are emerging that threaten everything from your financial credentials to your transit cards. Cybercrime is not a new industry. However, as technology is rapidly evolving, the ability of bad actors to compromise a digital identity is rapidly evolving.
With the latest data estimating that potential individual losses to cybercrime in the US totaled as high as $10 billion in 2022, a thought experiment is prevailing among cybersecurity stakeholders, as well as those studying an online Master's in Cybersecurity—what can be done to reduce, manage and mitigate the risks of compromised accounts for individuals—especially given the damaging impacts are well known?
One technology that has been gathering increased attention in recent months is the simple idea of increasing the number of factors that are used to authenticate a user—known as two-factor authentication (2FA) or, in some spaces, multi-factor authentication (MFA). Considered analogous to adding a second lock to a door, some organizations hold the view that this security system will be the future for accessing systems with secure content. Let's explore this technology and how it just may evolve how we interact with our accounts very soon.
The Challenge of Emerging Cyber Threats
Data breaches are becoming an ever-growing concern—no matter how large your organization may be, the underlying data is constantly under threat from challenges, both internal and external.
Many large organizations have faced the challenge of data breaches in the last year—from American Airlines to PayPal, it appears that no organization is immune to these attacks. For the individual who makes payments on PayPal, shops online at Forever 21, or buys flights with American Airlines, a single breach can lead to a complicated runaround of checking credentials for duplicated passwords, updating affected accounts, and then repeating the cycle all over with the next breach.
This constant cycle of learning about a breach, data defense, and tackling another breach can often lead to negative behaviors that impact your ability to stay secure online. Take, for example, the somewhat disconcerting statistic that six in ten Americans admit to reusing passwords—while more than nine in ten understand that reusing passwords represents a security risk. As cyber threats evolve, it has become critical for businesses to develop security strategies that attempt to mitigate the risk of poor employee behavior.
From SFA to 2FA
As a result of the volume of single-factor breaches that occur, many cybersecurity specialists are looking for economical ways to enhance login security in a way that is straightforward for employees to adopt while also gaining meaningful benefits from a risk perspective.
One proposed solution involves having a second type of authentication that employees must use when signing on to secure workplace systems. This authentication can come through in many ways, such as:
A time-sensitive generated code is sent to a user's mobile upon successful password entry.
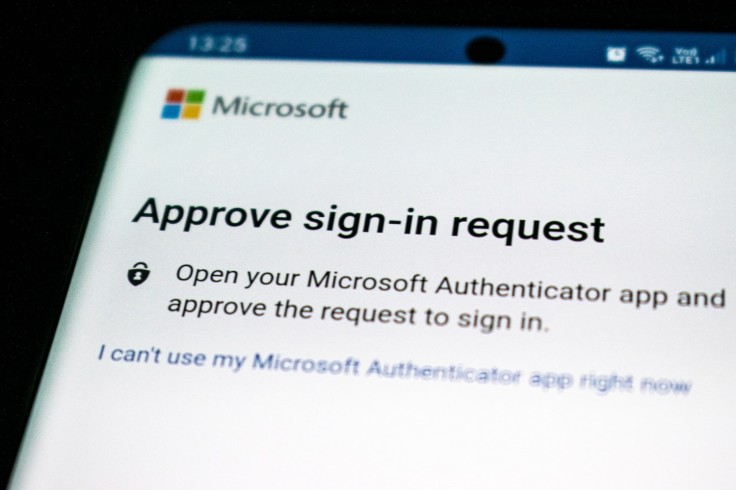
A time-sensitive push notification is sent to a user's work app upon successful password entry.
Two-factor authentication can have many benefits for those who are using the technology. For example, in today's world, where employees are highly mobile under remote working arrangements, an organization can be assured that a verified employee is securely using their credentials to access company records.
It can also make things a lot more difficult for a hacker to access. While a hacker may be able to get access to one compromised credential, such as a password, it can be much more difficult to gather access to an employee's device in a time-sensitive fashion. This increased security should not be underestimated—global tech titan Microsoft estimates that multi-factor authentication can help prevent as much as 99.9 percent of credential compromise attacks.
Multi-factor authentication typically refers to login security that contains two or more factors to authenticate a user. An organization is not limited to simply using a password and time-sensitive code for multi-factor authentication—many enterprises are now using a combination of IP address monitoring, device handshakes, and credential verification to provide an additional layer of security for employees. In some cases, this can also provide additional benefits—when an employee is working within the office, for example, they may be able to skip some authentication processes that are only necessary for external access.
Can 2FA Be Broken? The Risk of Cyber Complacency
While two-factor authentication yields great promise at being able to tackle some of the cyber security threats that present themselves to organizations, it is not immune to the risks present with any security technology. Three risks that arise when using 2FA technology include the loss of tokens, susceptibility to third-party disruption, and a lack of understanding of the benefits of the technology.
It's well understood that 2FA typically involves two or more separate devices—knowledge of a password, as well as access to a trusted device (such as a phone) that can prompt for a second authentication. However, in organizations where 2FA is not widely adopted, some account holders may find it difficult to remember to bring in their trusted device. Other users may not feel confident enough to use the platform and, as a result, may resist using 2FA entirely. Building up a trusted security culture and educating employees must form a critical component of any health cybersecurity culture in an organization.
The other main risks are closely intertwined. A poor understanding of the benefits of 2FA can lead to employees undertaking risky security behaviors—rather than storing a password securely. It may be stored as plaintext on a device that also contains a 2FA authenticator. 2FA can help to manage some of the symptoms of poor cyber health, but it cannot instantly protect an organization—employees must be aware that good password hygiene is just as important.
An employee, unaware that a two-factor authentication request comes through as a result of anyone successfully entering a password to their account, may accidentally approve a login request on a device that they do not own, leading to a security breach known as a fatigue attack.
While 2FA represents increased security benefits for organizations and their data, it's important that enterprise security teams still work to educate, train, and inform their employees of the cyber risks at play. Ignoring the current cyber landscape can be particularly perilous for those who hold sensitive data—ensure your employees are prepared for the challenges ahead.










