Ransomware attacks have been rampant lately, and Sobeys has been targeted as well. According to Bleeping Computer, the retail giant has been having issues with its IT systems starting last weekend, and Black Basta is to blame. As one of the major grocery retailers in Canada, Sobeys has around 1,500 stores scattered across ten provinces, and employs 134,000 workers.
The retail company run stores like Sobeys, Safeway, IGA, Foodland, FreshCo, Thrifty Foods, and Lawton Drugs. The grocery stores remain operational, yet some services have been affected by the issue with the IT systems. This was acknowledged through a press release published on Monday, by Sobey's parent company, Empire.
Problems Caused by the Ransomware
According to reports, the pharmacies under Sobeys have been experiencing technical difficulties. This has affected their services concerning prescription fulfillment. They added that the company will continue to be committed to taking care of their pharmacy patients. As of right now, the retail giant is working on its IT systems to avoid further disruptions.
A statement from Sobeys did express that the disruptions were not significant, yet employee reports have contradicted this. As stated by the workers, the affected stores of the retailer company had computers that were locked out. However, they were able to set up a separate network, which led to point-of-sale and payment processing systems being able to work.
Sobeys is not out of the woods yet, based on a confidentiality incident they sent to Quebec and Alberta privacy watchdogs. According to the reports from Canadian Press, personal information has been accessed by the hack, led by Black Basta ransomware. The hacker group released ransomware payloads that encrypt the systems on Sobeys' network.
A photo has been shared on a forum from redflagdeals.com, showing a ransom note from the attacker. It stated that data has been stolen and encrypted, Which will be made public on TOR website if the ransom was not paid.
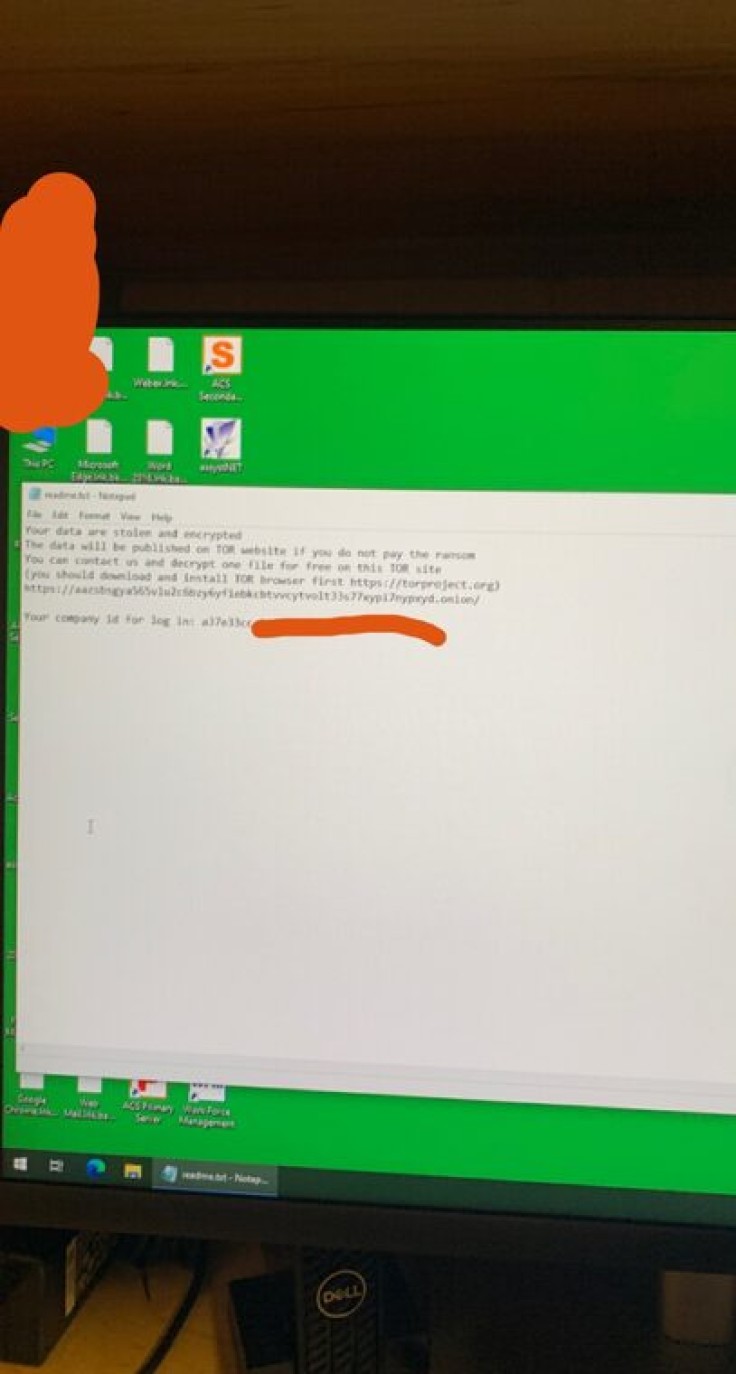
Black Basta Ransomware
The ransomware group operates as a ransomware-as-a-service (RaaS). They were first identified back in April 2022. According to Trend Micro, they use tools like Qakbot trojan and PrintNightmare exploit. The hacker group like other ransomware attackers, specifically targets their victims, instead of unleashing a widespread attack and hoping to get a hit.
The Black Basta ransomware group looks for corporate network access credentials on underground forums wherein they would demand a share of the profits from their hacks. Countries that may be attacked are the US, the UK, Canada, Australia, and New Zealand. There have been instances when a victim's data has already been published.
The American Dental Association (ADA) has already been subjected to a cyberattack, which affected multiple systems. The data stolen from the ADA was published just 96 hours after the hack. According to reports, Black Basta also had a Linux build of the ransomware, which encrypts VMware ESXi virtual machines. The build was discovered around June.









