Ransomware attacks are always bad news, whether it's from an experienced or new hacker group. The ransomware gang that Microsoft has been tracking proves that just because they have only emerged now, doesn't mean they aren't as dangerous as those who have conducted cyber attacks a hundred more times before.

Octo Tempest
If other threat actors have the patience to wait for the demanded ransom, this hacker group is the opposite. Instead of waiting for the victims to uphold their end of the bargain, Octo Tempest tries to expedite the exchange by using threats.
You can also tell that they don't do well with friendly negotiations, if there is such a thing with ransomware attacks. Instead of holding data hostage by encrypting it, Octo Tempest will simply threaten to release the data in public if the demanded ransom is not paid.
Like other threat actors, they also breach the defenses of their victims through the usual means such as social engineering, SMS phishing, SIM swaps, and more. Through SIM swapping, would be able to take over the accounts of its high-net-worth holder.
Upon gaining access, Octo Tempest will steal the cryptocurrency held in it. If not, the hackers will sell the unauthorized access through the swaps given that they are owned by mobile telecommunications processing services that handle other companies.
Microsoft says that "in rare instances, Octo Tempest resorts to fear-mongering tactics, targeting specific individuals through phone calls and texts." They would use the victim's personal information to intimidate them such as home addresses, family names, and more.
As shown in Ars Technica, the hacker group asked a victim to provide his login information or the hackers will get him fired. There was even a 10-minute ultimatum added to make it sound more threatening. When that did not work, the bad actor resorted to other threats.
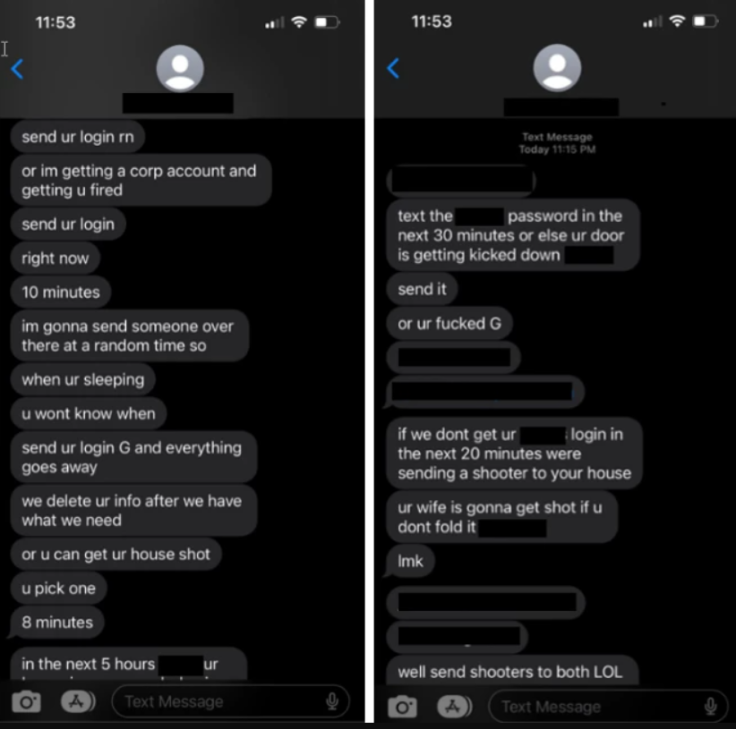
Other than counting down the minutes, the hackers said that they would get the victim's house shot. As they were continuously ignored, they threatened to kick the door down, send a shooter to the victim's house, or have his wife shot.
"In recent campaigns, we observed Octo Tempest leverage a diverse array of TTPs to navigate complex hybrid environments, exfiltrate sensitive data, and encrypt data," says the software giant. This includes SMS phishing, SIM swapping, and advanced social engineering techniques.
Targets and Tactics
The hacker group targets several industries including natural resources, gaming, hospitality, consumer products, retail, managed service providers, manufacturing, law, technology, and financial services.
Back in 2022, Octo Tempest only targeted mobile providers and business process outsources. They did it through SIM swapping, social engineering, and data collection. They will then commit cryptocurrency fraud and sell access.
Between late 2022 to early 2023, they started targeting telecommunication companies, as well as email and tech service providers. The hackers now do mass password resets and data exfiltration, with bigger goals like broad account takeover or leaking to large leak forums.
By 2023, Microsoft states that they have reached industries like gaming, hospitality, manufacturing, technology, finance, and more. As a BlackCat affiliate, they moved on to extortion using encrypted data and data theft as leverage.









